|
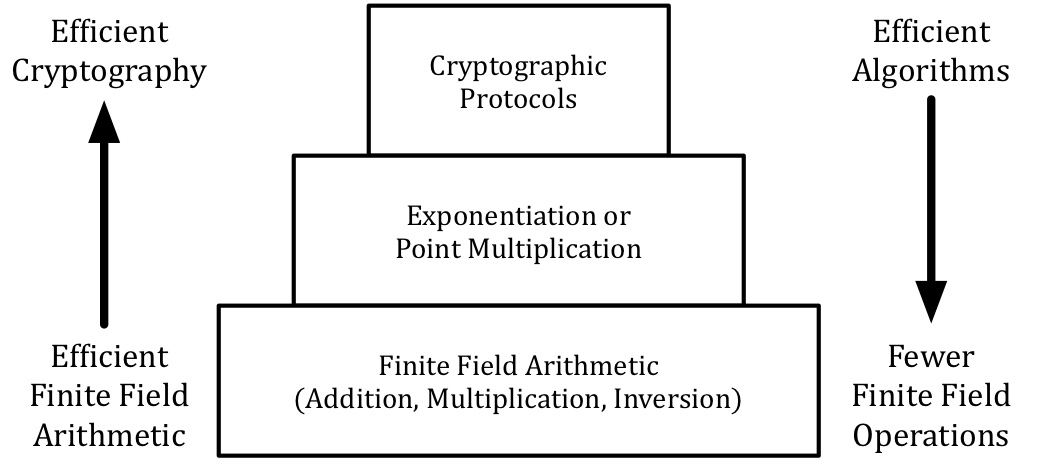
We have made significant contributions to finite field arithmetic, and continue to invent new algorithms and architectures.
Selected Publications
- Ç. K. Koç.
Algorithms for inversion mod p^k.
IEEE Transactions on Computers,
69(6): 907-913, June 2020.
pdf
- W. Dai, D. D. Chen, R. C. C. Cheung, and Ç. K. Koç.
Area-time efficient architecture of FFT-based Montgomery multiplication.
IEEE Transactions on Computers, 66(3):375-388, March 2017.
pdf
- D. D. Chen, G. X. Yao, R. C. C. Cheung, D. Pao, and
Ç. K. Koç. Parameter space for the architecture of
FFT-based Montgomery modular multiplication.
IEEE Transactions on Computers, 65(1):147-160, January 2016.
pdf
- Ç. K. Koç.
Introduction to the Journal of Cryptographic Engineering.
Journal of Cryptographic Engineering,
1(1):1-3, April 2011.
pdf
- E. Savaş and Ç. K. Koç.
Finite field arithmetic for cryptography.
IEEE Circuits and Systems Magazine,
10(2):40-56, 2010.
pdf
- A. F. Tenca, E. Savaş, and Ç. K. Koç.
A design framework for scalable and unified multipliers
in GF(p) and GF(2^m).
International Journal of Computer Research,
13(1):68-83, 2004.
pdf
- A. F. Tenca and Ç. K. Koç.
A scalable architecture for modular multiplication based
on Montgomery's algorithm.
IEEE Transactions on Computers,
52(9):1215-1221, September 2003.
pdf
- Ç. K. Koç and T. Acar.
Montgomery multiplication in GF(2^k).
Designs, Codes and Cryptography, 14(1):57-69, April 1998.
pdf
→
Random Number Generators
|